Atlassian Synology Dragon Quest Stage 1+2
SummaryIn this article I am taking the
Atlassian Dragon Quest and implement the full JIRA Suite:
On a vanilla Synology DS1511+ NAS with 3Gb memory.
Intended audienceAudience is every DS1010+ & DS1511+ (future) Owner who likes to do development on his NAS. I’m not expecting it to handle 100’s of developers, however for the 1-10 users my guess is: it’s a fine setup.
IntroductionThe
DS1511+ &
DS1010+ are Intel Atom based systems, fully x86-64 compatible running a stripped down version of linux x64. The default configuration comes with 1Gb and is official expandable to 3Gb. However also working configurations of 5Gb have been reported.
For an install with only Jira, the 1Gb is sufficient and it even doesn’t need to be
bootstrapped since Jira comes with its own JRE & Tomcat + we can use the internal MySQL database.
For the complete dragon Quest, I’ve upgraded the DS1511+ with an additional 2Gb from
Kingston SODIMM DDR2-800 2GB CL5.0 (KVR800D2S5/2G). The Original memory module is €82, The Kingston is €21 so take your pick ;-).
I’ve tried to run Jira + FishEye with 1Gb and it just is to tight. Perhaps if you tweak it’s memory usages it might work. However better spend 21 buck on a memory upgrade and save your self the day(s) of trouble.
Let’s step back and analyse our playing field and potential pitfalls
The Synology OS (DSM 3.2) comes with two internal databases: MySQL and Postgres. Both are used internally and are configured for light internal use only. They are trimmed down in memory usages and not configured for heavy query material.
=>
The previous proof-of-concept install with the internal MySQL I learned the internal MySQL db is hard to tweak and “if” I tweaked it, the tweaks are reversed after each upgrade of the DSM.
For the sake of Freedom: We will use a dedicated stand alone install of Postgresql.
Preparation of the Synology Dragon’s Lair
Bootstrap
First we are going to prepare the vanilla Synology for some serious work. Enable SSH and login in as root on your NAS which has the same password as your admin from the webinterface.
Login as admin on the webinterface: ControlPanel->Teminal -> [X] Enable SSH service
We are now downloading the bootstrap, please make sure you have the latest version.
ssh root@_your_nas_ip
wget http://ipkg.nslu2-linux.org/feeds/optware/syno-i686/cross/stable/syno-i686-bootstrap_1.2-7_i686.xsh
chmod 700 syno-i686-bootstrap_1.2-7_i686.xsh
./syno-i686-bootstrap_1.2-7_i686.xsh
ipkg update
ipkg install bash
ipkg install coreutils
ipkg install man
Now make your choice on your SCM ( cvs, svn, grit … ) I’ll pick SVN
ipkg install svn For setup svn on the NAS look here:
Congratulations! Your preparation is finished! We can now start with the Dragon’s Quest!

Check your self in on twitter for the Quest on the Dragon’s Quest Page HERE.
We will follow the instructions step by step and adjust it for the Synology.
Step 1. Install Java
Read the instructions of step 1 On the Synology we do not install the java binary blindly since the
/root partition is only limited in size, we are installing it on the /opt directory with a symbolic link to
/opt/java and set the
JAVA_HOME to the
/opt/java On September 11th 2011 Java 7 did not work on the Synology DSM 3.2, Java 1.6.27 does!
Unpack it in /opt and make a symbolic link to java.
ln -s /opt/jdk1.6.0_27 /opt/java
Add java to the path and set
JAVA_HOME in the
/etc/profile file
vi /etc/profilePATH=/opt/bin:/opt/sbin:/opt/java/bin:$PATH
JAVA_HOME=/opt/java/
export JAVA_HOME Step 1/Stage 1 is complete now!
Step 2 Install your PostgreSQL Database ServerReview step 2 Get the
pgadmin client for your Linux/Mac desktop it will be used later on in the Quest.
Install the stand alone and independent Postgres:
ipkg install postgresql
READ the text after the install is finished!
mv /opt/etc/init.d/S98postgresql /usr/local/etc/rc.d/S22postgresql.sh
Do not use the /opt/etc/init.d/ for starting & stopping Postgresql, init.d only start services but does not stop them correctly!. It might destroy your database if it is not shutdown properly!
Since there is already a Postgres running internally we are going to move the postgres port from 5432 into 54320.
vi /opt/var/pgsql/data/postgresql.conf
Change the line that reads:
#port = 5432 and change it into:
port = 54320
Consider, Setting the
listen_addresses=’*’ and
edit the
pg_hba.conf for remote access and add your desktop ip (
192.168.1.101/32 for example) to the file some thing like:
host all all
192.168.1.101/32 trust
Restart Postgresql
/usr/local/etc/rc.d/S22postgresql.sh restart
Use pgadmin to connect to your postgres database
(hint! postgresql port is @54320 not the default port @5432 😉 that’s the system’s database)
Step 3 Create your JIRA Database in PostgreSQL Read and apply step 3No changes needed for the Synology.
Step 4 Install JIRA
Preprerations, creating the user & environment:
vi /etc/passwd
add the line:
jira:x:403:400:Jira:/volume1/@atlassian/jira:/opt/bin/bash
vi /etc/shaddow
add the line:
jira:*:10933:0:99999:7:::
vi /etc/group
add the line:
atlassian:x:400:jira
We don’t use the installer, we need to manual install it.Go to the download centre and get the tar.gz 32b version:
http://www.atlassian.com/software/jira/downloads/binary/atlassian-jira-4.4.tar.gz Download the file and unpack it.
mkdir /volume1/@atlassian
cp ~/atlassian-jira-4.4.tar.gz /volume1/@atlassian cd /volume1/@atlassian
copy the JIRA tar into the directory and unpack.
tar zxvf atlassian-jira-4.4.tar.gz
Rename and chown the directory
mv atlassian-jira-4.4-standalone/ jirachown -R jira:atlassian jira
set the
JIRA_HOME mkdir /volume1/@atlassian/application-data/
chown jira:atlassian /volume1/@atlassian/application-data/
chmod 770 /volume1/@atlassian/application-data
vi ./atlassian-jira/WEB-INF/classes/jira-application.properties
jira.home = /volume1/@atlassian/application-data/jira
Adjust the start and stop script
vi /volume1/@atlassian/jira/bin/start-jira.sh vi /volume1/@atlassian/jira/bin/stop-jira.sh
change the first line in both
start-jira.sh and
stop-jira.sh #!/bin/bash into
#!/opt/bin/bash
Change in both files also the line:
sucmd=”su”
into
sucmd=”/opt/bin/su”Check if this file
su exists.
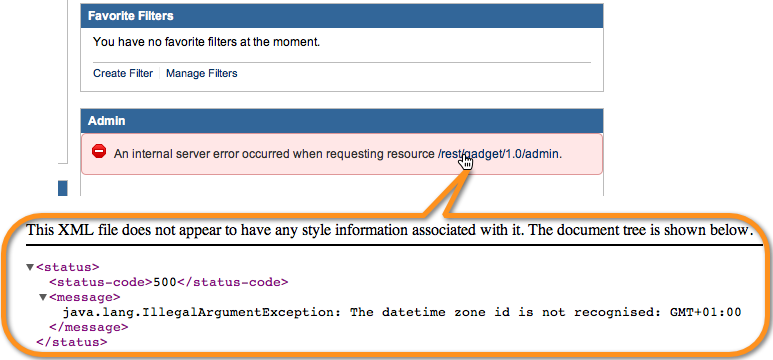
Also set your timezone correct, (see also the topic
BUG Workaround here)
vi /volume1/@atlassian/jira/bin/setenv.sh Find the line that reads:
JVM_SUPPORT_RECOMMENDED_ARGS=”” And add
-Duser.timezone= with your time zone in the
Canonical ID format.
For example Amsterdam would be:
JVM_SUPPORT_RECOMMENDED_ARGS=”-Duser.timezone=Europe/Amsterdam”
Set the default user for the process:
vi /volume1/@atlassian/jira/bin/user.sh Change the line:
JIRA_USER=”” ##into
JIRA_USER=”jira” ## ( yes it says don’t edit, do it anyway )
Create a
rc.d script that starts/stops JIRA:
vi /usr/local/etc/rc.d/S95jira.sh
#!/opt/bin/bash
# JIRA Linux service controller script
# Set private environment, check if they apply for you.
JAVA_HOME=”/opt/java”
PATH=$PATH:/opt/java/bin
export JAVA_HOME PATH
cd “/volume1/@atlassian/jira/bin”
case “$1” in
start)
./start-jira.sh
;;
stop)
./stop-jira.sh
;;
*)
echo “Usage: $0 {start|stop}”
exit 1
;;
esac
chmod 755 /usr/local/etc/rc.d/S95jira.sh
Now reboot your NAS and see if the services Postgres & Jira come up
http://<your NAS ip>:8080/
Integrating Jira with Apache on HTTP *:80Open the server.xml file and adjust:
vi /volume1/@atlassian/jira/conf/server.xml
Find the line that reads:
<Context path=”” docBase=”${catalina.home}/atlassian-jira” reloadable=”false” useHttpOnly=”true”>
And change it into:
<Context path=”/jira” docBase=”${catalina.home}/atlassian-jira” reloadable=”false” useHttpOnly=”true”>
Now create a new file:
vi /usr/syno/apache/conf/jira-mod_proxy
And place the following content in it:
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_ajp_module modules/mod_proxy_ajp.so
LoadModule proxy_http_module modules/mod_proxy_http.so
<Proxy *>
Order deny,allow
Allow from all
</Proxy>
ProxyRequests Off
ProxyPreserveHost On
ProxyPass /jira http://localhost:8080/jira
ProxyPassReverse /jira http://localhost:8080/jira
Write the file to:
/usr/syno/apache/conf/jira-mod_proxy
Now open the file:
vi /usr/syno/apache/conf/httpd.conf-user
And add a last line:
Include conf/jira-mod_proxy
Reboot your NAS
( or /usr/syno/apache/bin/httpd -k restart ) And point your browser to:
http://<your host name>/jira
And enjoy what unfolds!
Integrating Jira with Apache on HTTPS: *:443
Client Browser --> HTTPS --> Apache proxy --> HTTP --> Tomcat/JIRAFollow the steps in this document how to set up:Atlassian: Integrating+JIRA+with+Apache+using+SSL
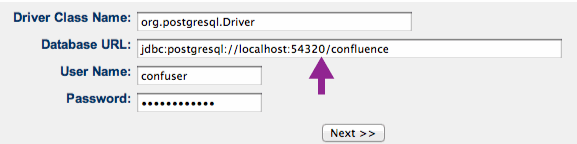
vi /volume1/@atlassian/confluence/conf/server.xml
Add the last three lines to the connector and change the port into 8080
<Connector port="8080" protocol="HTTP/1.1"
connectionTimeout="20000"
redirectPort="8443"
URIEncoding="UTF-8"
useBodyEncodingForURI="true"
scheme="https"
proxyName="<proxy_server>"
proxyPort="443"
/>
Import your public key into the java key store and restart confluence:
Atlassian: Integrating+JIRA+with+Apache+using+SSL
Create a new file for httpd:
vi /usr/syno/apache/conf/jira-ssl.confAnd place the following content in it:
# Jira Proxy Setup
# J.W. de Roode Sep11
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_ajp_module modules/mod_proxy_ajp.so
LoadModule proxy_http_module modules/mod_proxy_http.so
LoadModule ssl_module modules/mod_ssl.so
Listen 443
AddType application/x-x509-ca-cert .crt
AddType application/x-pkcs7-crl .crl
SSLPassPhraseDialog builtin
SSLSessionCache none
SSLSessionCacheTimeout 3600
SSLMutex file:/var/tmp/ssl_mutex-user
SSLCipherSuite HIGH:MEDIUM:!RC4:!aNULL
SSLProtocol all -SSLv2
SSLCertificateFile /usr/syno/etc/ssl/ssl.crt/server.crt
SSLCertificateKeyFile /usr/syno/etc/ssl/ssl.key/server.key
##
## SSL Virtual Host Context
##
<VirtualHost *:443>
SSLEngine on
<FilesMatch “.(cgi|shtml|phtml|php)$”>
SSLOptions +StdEnvVars
</FilesMatch>
BrowserMatch “.*MSIE.*”
nokeepalive ssl-unclean-shutdown
downgrade-1.0 force-response-1.0
CustomLog /dev/null
“%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x “%r” %b”
<Proxy *>
Order deny,allow
Allow from all
</Proxy>
ProxyRequests Off
ProxyPreserveHost On
ProxyPass /jira http://localhost:8080/jira
ProxyPassReverse /jira http://localhost:8080/jira
</VirtualHost>
Open the file:
vi /usr/syno/apache/conf/httpd.conf-user
And add/replace the last lines:
#Include conf/jira-mod_proxy # HTTP Config
Include conf/jira-ssl.conf # HTTPS Config
Reboot your NAS
( or /usr/syno/apache/bin/httpd -k restart ) And point your browser to:
https://<your host name>/jira
And enjoy what unfolds!
Follow-up on the
Dragon Quest assignments of stage 1 and Tweet the completion on twitter.
Dragon Stage 2 – Set Up GreenHopper in JIRAFollow the steps in the document of Stage 2 of the Dragons.
Next post will handle stage 3 – Install Confluence